
Avoid to content
CONCERNING A PHONE NEAR YOU
New style sets a high requirement for post-quantum preparedness.

Credit: Aurich Lawson|Getty Images
Credit: Aurich Lawson|Getty Images
The file encryption safeguarding interactions versus criminal and nation-state sleuthing is under hazard. As personal market and federal governments get closer to constructing helpful quantum computer systems, the algorithms securing Bitcoin wallets, encrypted web gos to, and other delicate tricks will be worthless. Nobody questions the day will come, however as the now-common joke in cryptography circles observes, specialists have actually been anticipating this cryptocalypse will get here in the next 15 to 30 years for the previous 30 years.
The unpredictability has developed something of an existential predicament: Should network designers invest the billions of dollars needed to wean themselves off quantum-vulnerable algorithms now, or should they prioritize their restricted security spending plans battling more instant hazards such as ransomware and espionage attacks? Offered the cost and no clear due date, it’s little marvel that less than half of all TLS connections made inside the Cloudflare network and just 18 percent of Fortune 500 networks support quantum-resistant TLS connections. It’s all however particular that lots of less companies still are supporting quantum-ready file encryption in less popular procedures.
Accomplishment of the cypherpunks
One exception to the industry-wide sleepiness is the engineering group that creates the Signal Protocol, the open source engine that powers the world’s most robust and durable kind of end-to-end file encryption for several personal chat apps, most especially the Signal Messenger. Eleven days earlier, the not-for-profit entity that establishes the procedure, Signal Messenger LLC, released a 5,900-word article explaining its most current updates that bring Signal a considerable action towards being completely quantum-resistant.
The intricacy and analytical needed for making the Signal Protocol quantum safe are as intimidating as practically any in modern-day engineering. The initial Signal Protocol currently looked like the within a great Swiss watch, with numerous equipments, wheels, springs, hands, and other parts all interoperating in an elaborate method. In less proficient hands, mucking about with an instrument as complex as the Signal procedure might have caused faster ways or unintentional effects that harm efficiency, undoing what would otherwise be a completely running watch. This newest post-quantum upgrade (the very first one came in 2023) is absolutely nothing brief of an accomplishment.
“This seems a strong, thoughtful enhancement to the existing Signal Protocol,” stated Brian LaMacchia, a cryptography engineer who managed Microsoft’s post-quantum shift from 2015 to 2022 and now operates at Farcaster Consulting Group. “As part of this work, Signal has actually done some intriguing optimization under the hood so regarding lessen the network efficiency effect of including the post-quantum function.”
Of the numerous difficulties to clear, the most difficult was representing the much bigger essential sizes that quantum-resistant algorithms need. The overhaul here includes securities based upon ML-KEM-768, an application of the CRYSTALS-Kyber algorithm that was chosen in 2022 and formalized in 2015 by the National Institute of Standards and Technology. ML-KEM is brief for Module-Lattice-Based Key-Encapsulation Mechanism, however the majority of the time, cryptographers describe it just as KEM.
Cogs, ping-pong, and asynchrony
Like the Elliptic curve Diffie-Hellman (ECDH) procedure that Signal has actually utilized given that its start, KEM is an essential encapsulation system. Understood as an essential contract system, it offers the ways for 2 celebrations who have actually never ever fulfilled to firmly concur on one or more shared tricks in the existence of a foe who is keeping track of the celebrations’ connection. RSA, ECDH, and other encapsulation algorithms have actually long been utilized to work out symmetric secrets (usually AES secrets) in procedures consisting of TLS, SSH, and IKE. Unlike ECDH and RSA, nevertheless, the much more recent KEM is quantum-safe.
Secret contract in a procedure like TLS is fairly uncomplicated. That’s due to the fact that gadgets linking over TLS work out a secret over a single handshake that takes place at the start of a session. The agreed-upon AES secret is then utilized throughout the session. The Signal Protocol is various. Unlike TLS sessions, Signal sessions are safeguarded by forward secrecy, a cryptographic residential or commercial property that guarantees the compromise of a crucial utilized to secure a current set of messages can’t be utilized to decrypt an earlier set of messages. The procedure likewise provides Post-Compromise Security, which safeguards future messages from previous essential compromises. While a TLS utilizes the exact same secret throughout a session, secrets within a Signal session continuously progress.
To offer these privacy warranties, the Signal Protocol updates secret crucial product each time a message celebration strikes the send out button or gets a message, and at other points, such as in visual signs that a celebration is presently typing and in the sending out of read invoices. The system that has actually made this continuous essential development possible over the previous years is what procedure designers call a “double cog.” Simply as a conventional cog permits an equipment to turn in one instructions however not in the other, the Signal cogs permit messaging celebrations to produce brand-new secrets based upon a mix of preceding and freshly agreed-upon tricks. The cogs operate in a single instructions, the sending out and getting of future messages. Even if a foe jeopardizes a freshly produced trick, messages secured utilizing older tricks can’t be decrypted.
The beginning point is a handshake that carries out 3 or 4 ECDH arrangements that blend long- and short-term tricks to develop a shared trick. The development of this “root key” permits the Double Ratchet to start. Till 2023, the essential contract utilized X3DH. The handshake now utilizes PQXDH to make the handshake quantum-resistant.
The very first layer of the Double Ratchet, the Symmetric Ratchet, obtains an AES secret from the root secret and advances it for each message sent out. This permits every message to be secured with a brand-new secret key. If opponents compromise one celebration’s gadget, they will not be able to discover anything about the secrets that came earlier. Even then, however, the assaulters would still have the ability to calculate the secrets utilized in future messages. That’s where the 2nd,” Diffie-Hellman cog” is available in.
The Diffie-Hellman cog integrates a brand-new ECDH public secret into each message sent out. Utilizing Alice and Bob, the imaginary characters typically described when discussing uneven file encryption, when Alice sends out Bob a message, she develops a brand-new cog keypair and calculates the ECDH arrangement in between this secret and the last ratchet public crucial Bob sent out. This offers her a brand-new trick, and she understands that when Bob gets her brand-new public secret, he will understand this trick, too (because, as discussed previously, Bob formerly sent out that other secret). With that, Alice can blend the brand-new trick with her old root secret to get a brand-new root secret and begin fresh. The outcome: Attackers who discover her old tricks will not have the ability to discriminate in between her brand-new cog secrets and random sound.
The outcome is what Signal designers refer to as “ping-pong” habits, as the celebrations to a conversation take turns changing ratchet essential sets one at a time. The result: An eavesdropper who jeopardizes among the celebrations may recuperate a present cog personal secret, however quickly enough, that personal secret will be changed with a brand-new, uncompromised one, and in such a way that keeps it devoid of the spying eyes of the opponent.
The goal of the freshly created secrets is to restrict the variety of messages that can be decrypted if an enemy recuperates crucial product at some time in a continuous chat. Messages sent out prior to and after the compromise will stay off limitations.
A significant difficulty designers of the Signal Protocol face is the requirement to make the cogs operate in an asynchronous environment. Asynchronous messages happen when celebrations send out or get them at various times– such as while one is offline and the other is active, or vice versa– without either requiring to be present or react instantly. The whole Signal Protocol need to work within this asynchronous environment. What’s more, it needs to work dependably over unsteady networks and networks managed by foes, such as a federal government that requires a telecom or cloud service to spy on the traffic.
Shor’s algorithm hiding
By all accounts, Signal’s double ratchet style is advanced. That stated, it’s broad open to an unavoidable if not instant risk: quantum computing. That’s due to the fact that a foe efficient in keeping track of traffic passing from 2 or more messenger users can record that information and feed it into a quantum computer system– as soon as among adequate power is feasible– and determine the ephemeral secrets created in the 2nd cog.
In classical computing, it’s infeasible, if not difficult, for such an enemy to determine the secret. Like all uneven file encryption algorithms, ECDH is based upon a mathematical, one-way function. Understood as trapdoor functions, these issues are insignificant to calculate in one instructions and significantly more difficult to calculate in reverse. In elliptic curve cryptography, this one-way function is based upon the Discrete Logarithm issue in mathematics. The essential criteria are based upon particular points in an elliptic curve over the field of integers modulo some prime P.
Usually, an enemy geared up with just a classical computer system would invest billions of years thinking integers before coming to the best ones. A quantum computer system, by contrast, would have the ability to determine the appropriate integers in a matter of hours or days. A formula called Shor’s algorithm– which runs just on a quantum computer system– reverts this one-way discrete logarithm formula to a two-way one. Shor’s Algorithm can likewise make fast work of fixing the one-way function that’s the basis for the RSA algorithm.
As kept in mind previously, the Signal Protocol got its very first post-quantum remodeling in 2023. This upgrade included PQXDH– a Signal-specific execution that integrated the essential contracts from elliptic curves utilized in X3DH (particularly X25519) and the quantum-safe KEM– in the preliminary procedure handshake. (X3DH was then put out to pasture as a standalone execution.)
The relocation foreclosed the possibility of a quantum attack having the ability to recuperate the symmetric secret utilized to begin the cogs, however the ephemeral secrets developed in the ping-ponging 2nd cog stayed susceptible to a quantum attack. Signal’s most current upgrade includes quantum resistance to these secrets, guaranteeing that forward secrecy and post-compromise security are safe from Shor’s algorithm.
Despite the fact that the ping-ponging secrets are susceptible to future quantum attacks, they are broadly thought to be safe and secure versus today’s attacks from classical computer systems. The Signal Protocol designers didn’t wish to eliminate them or the battle-tested code that produces them. That resulted in their choice to include quantum resistance by including a 3rd cog. This one utilizes a quantum-safe KEM to produce brand-new tricks similar to the Diffie-Hellman cog did previously, guaranteeing quantum-safe, post-compromise security.
The technical obstacles were anything however simple. Elliptic curve secrets created in the X25519 execution have to do with 32 bytes long, little enough to be contributed to each message without producing a concern on currently constrained bandwidths or calculating resources. A ML-KEM 768 secret, by contrast, is 1,000 bytes. In addition, Signal’s style needs sending out both a file encryption secret and a ciphertext, making the overall size 2272 bytes.
And after that there were 3
To deal with the 71x boost, Signal designers thought about a range of choices. One was to send out the 2272-byte KEM secret less typically– state every 50th message or as soon as weekly– instead of every message. That concept was nixed since it does not work well in asynchronous or adversarial messaging environments. Signal Protocol designers Graeme Connell and Rolfe Schmidt described:
Think about the case of “send out an essential if you have not sent out one in a week”. If Bob has been offline for 2 weeks, what does Alice do when she wishes to send out a message? What takes place if we can lose messages, and we lose the one in fifty which contains a brand-new secret? Or, what occurs if there’s an aggressor in the middle that wishes to stop us from producing brand-new tricks, and can try to find messages that are [many] bytes bigger than the others and drop them, just permitting keyless messages through?
Another choice Signal engineers thought about was breaking the 2272-byte secret into smaller sized pieces, state 71 of them that are 32 bytes each. Separating the KEM secret into smaller sized pieces and putting one in each message seems like a feasible method in the beginning, once again, the asynchronous environment of messaging made it impracticable. What occurs, for instance, when information loss triggers among the portions to be dropped? The procedure might handle this situation by simply repeat-sending pieces once again after sending out all 71 formerly. Then a foe keeping track of the traffic might merely trigger package 3 to be dropped each time, avoiding Alice and Bob from finishing the essential exchange.
Signal designers eventually opted for a service that utilized this multiple-chunks technique.
Slipping an elephant through the feline door
To handle the asynchrony obstacles, the designers turned to “erasure codes,” a technique of separating bigger information into smaller sized pieces such that the original can be rebuilded utilizing any adequately sized subset of portions.
Charlie Jacomme, a scientist at INRIA Nancy on the Pesto group who concentrates on official confirmation and protected messaging, stated this style represent package loss by developing redundancy into the chunked product. Rather of all x variety of pieces needing to be effectively gotten to rebuild the secret, the design needs just x-y portions to be gotten, where y is the appropriate variety of packages lost. As long as that limit is fulfilled, the brand-new secret can be developed even when package loss happens.
The other part of the style was to divide the KEM calculations into smaller sized actions. These KEM calculations stand out from the KEM crucial product.
As Jacomme described it:
Basically, a little part of the general public secret suffices to begin calculating and sending out a larger part of the ciphertext, so you can rapidly send out in parallel the remainder of the public secret and the start of the ciphertext. Basically, the last calculations amount to the requirement, however some things was parallelized.
All this in truth contributes in the end security warranties, due to the fact that by enhancing the truth that KEM calculations are done much faster, you present in your crucial derivation fresh tricks more often.
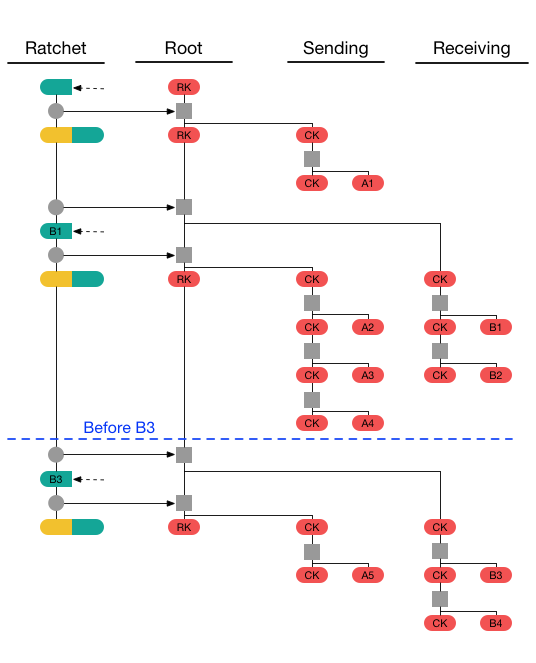
Signal’s post 10 days ago consisted of a number of images that highlight this style:
While the style resolved the asynchronous messaging issue, it produced a brand-new problem of its own: This brand-new quantum-safe cog advanced so rapidly that it could not be kept integrated with the Diffie-Hellman cog. Eventually, the designers picked an innovative option. Instead of bolt KEM onto the existing double cog, they permitted it to stay basically the like it had actually been. They utilized the brand-new quantum-safe cog to execute a parallel protected messaging system.
Now, when the procedure secures a message, it sources file encryption secrets from both the traditional Double Ratchet and the brand-new cog. It then blends the 2 secrets together (utilizing a cryptographic crucial derivation function) to get a brand-new file encryption secret that has all of the security of the classical Double Ratchet and now has quantum security, too.
The Signal engineers have actually offered this 3rd cog the official name: Sparse Post Quantum Ratchet, or SPQR for brief. The 3rd cog was created in cooperation with PQShield, AIST, and New York University. The designers provided the erasure-code-based chunking and the top-level Triple Ratchet style at the Eurocrypt 2025 conference. At the Usenix 25 conference, they went over the 6 choices they thought about for including quantum-safe forward secrecy and post-compromise security and why SPQR and another stood apart. Discussions at the NIST PQC Standardization Conference and the Cryptographic Applications Workshop describe the information of chunking, the style difficulties, and how the procedure needed to be adjusted to utilize the standardized ML-KEM.
Jacomme even more observed:
The last thing fascinating for the triple cog is that it perfectly integrates the very best of both worlds. In between 2 users, you have a classical DH-based cog going on one side, and completely individually, a KEM-based cog is going on. Whenever you require to secure something, you get a secret from both, and blend it up to get the real file encryption secret. Even if one cog is totally broken, be it due to the fact that there is now a quantum computer system, or due to the fact that someone handles to break either elliptic curves or ML-KEM, or due to the fact that the application of one is flawed, or …, the Signal message will still be safeguarded by the 2nd cog. In a sense, this upgrade can be seen, naturally streamlining, as doubling the security of the ratchet part of Signal, and is a cool thing even for individuals that do not care about quantum computer systems.
As both Signal and Jacomme kept in mind, users of Signal and other messengers counting on the Signal Protocol need not worry themselves with any of these brand-new styles. To paraphrase a specific gadget maker, it simply works.
In the coming weeks or months, numerous messaging apps and app variations will be upgraded to include the triple cog. Up until then, apps will merely depend on the double cog as they constantly did. As soon as apps get the upgrade, they’ll act precisely as they did before updating.
For those who appreciate the internal functions of their Signal-based apps, however, the designers have actually recorded in excellent depth the style of this brand-new cog and how it acts. To name a few things, the work consists of a mathematical evidence validating that the upgraded Signal procedure supplies the declared security homes.
Outdoors scientists are praising the work.
“If the typical encrypted messages we utilize are felines, then post-quantum ciphertexts are elephants,” Matt Green, a cryptography specialist at Johns Hopkins University, composed in an interview. “So the issue here is to slip an elephant through a tunnel created for felines. Which’s a fantastic engineering accomplishment. It likewise makes me want we didn’t have to deal with elephants.”
Dan Goodin is Senior Security Editor at Ars Technica, where he manages protection of malware, computer system espionage, botnets, hardware hacking, file encryption, and passwords. In his extra time, he takes pleasure in gardening, cooking, and following the independent music scene. Dan is based in San Francisco. Follow him at here on Mastodon and here on Bluesky. Contact him on Signal at DanArs.82.
94 Comments
Find out more
As an Amazon Associate I earn from qualifying purchases.








