Screenshot revealing a chart tracking mining activity.
Credit: Checkmarx
Wait, there’s more
On Friday, Datadog exposed that MUT-1244 utilized extra methods for installing its second-stage malware. One was through a collection of a minimum of 49 harmful entries published to GitHub which contained Trojanized proof-of-concept exploits for security vulnerabilities. These bundles assist harmful and kindhearted security workers much better comprehend the level of vulnerabilities, consisting of how they can be made use of or covered in real-life environments.
A 2nd significant vector for spreading out @ 0xengine/xmlrpc was through phishing e-mails. Datadog found MUT-1244 had actually left a phishing design template, accompanied by 2,758 e-mail addresses scraped from arXiv, a website often visited by expert and scholastic scientists.
A phishing e-mail utilized in the project.
Credit: Datadog
The e-mail, directed to individuals who establish or research study software application for high-performance computing, motivated them to set up a CPU microcode upgrade offered that would considerably enhance efficiency. Datadog later on identified that the e-mails had actually been sent out from October 5 through October 21. 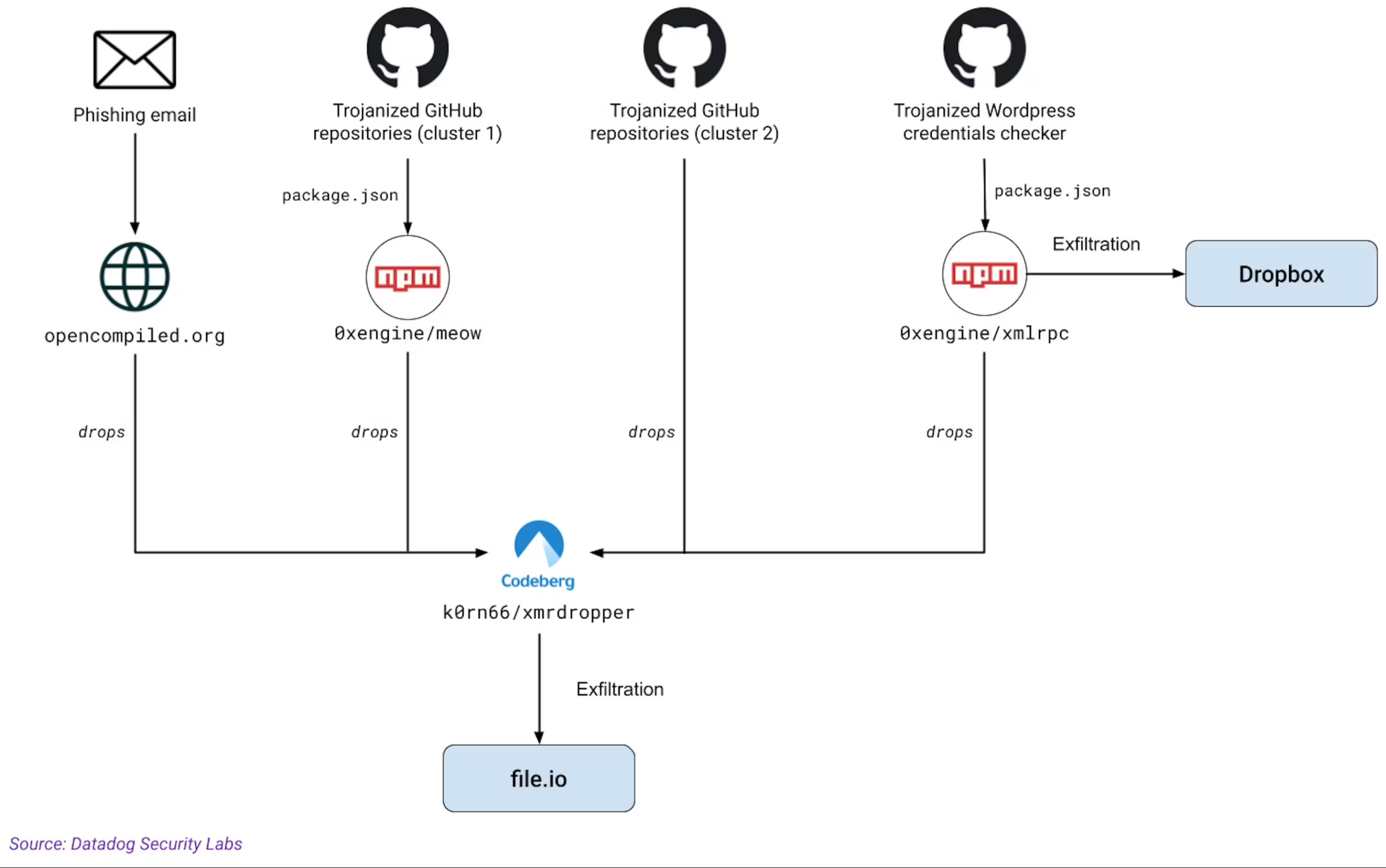
Extra vectors found by Datadog.
Credit: Datadog
More contributing to the impression of authenticity, numerous of the destructive plans are instantly consisted of in genuine sources, such as Feedly Threat Intelligence and Vulnmon. These websites consisted of the destructive plans in proof-of-concept repositories for the vulnerabilities the plans declared to make use of.
“This increases their look of legitimacy and the likelihood that someone will run them,” Datadog stated.
The opponents’ usage of @ 0xengine/xmlrpc enabled them to take some 390,000 qualifications from contaminated makers. Datadog has actually figured out the qualifications were for usage in logging into administrative represent sites that run the WordPress material management system.
Taken together, the numerous aspects of the project– its durability, its accuracy, the expert quality of the backdoor, and its several infection vectors– show that MUT-1244 was a competent and figured out risk star. The group did, nevertheless, err by leaving the phishing e-mail design template and addresses in an openly readily available account.
The supreme intentions of the aggressors stay uncertain. If the objective were to mine cryptocurrency, there would likely be much better populations than security workers to target. And if the goal was targeting scientists– as other just recently found projects have actually done– it’s uncertain why MUT-1244 would likewise use cryptocurrency mining, an activity that’s frequently simple to discover.
Reports from both Checkmarx and Datadog consist of indications individuals can utilize to examine if they’ve been targeted.
Find out more
As an Amazon Associate I earn from qualifying purchases.