As an Amazon Associate I earn from qualifying purchases.
Pestering out–
Redmond wishes to enhance the strength of Windows to buggy software application.
Stephanie Stacey and Richard Waters, FEET
–
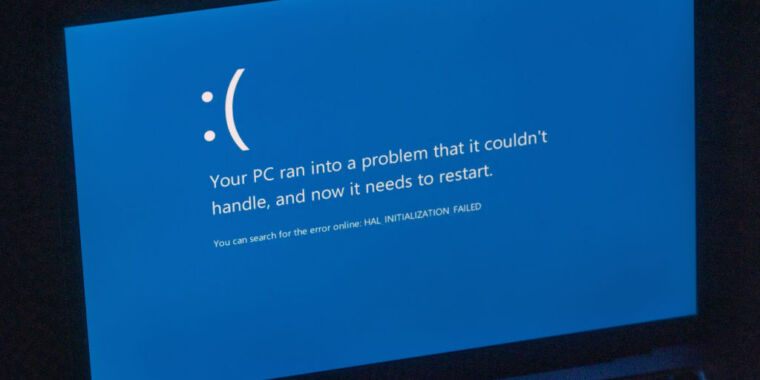
Microsoft is stepping up its strategies to make Windows more durable to buggy software application after a messed up CrowdStrike upgrade removed countless PCs and servers in an international IT blackout.
The tech giant has in the previous month magnified talks with partners about adjusting the security treatments around its os to much better hold up against the sort of software application mistake that crashed 8.5 million Windows gadgets on July 19.
Critics state that any modifications by Microsoft would total up to a concession of drawbacks in Windows’ handling of third-party security software application that might have been resolved faster.
They would likewise show questionable amongst security suppliers that would have to make extreme modifications to their items, and require lots of Microsoft consumers to adjust their software application.
Last month’s failures– which are approximated to have actually triggered billions of dollars in damages after grounding countless flights and interfering with medical facility consultations worldwide– increased analysis from regulators and magnate over the degree of gain access to that third-party software application suppliers need to the core, or kernel, of Windows running systems.
Microsoft will host a top next month for federal government agents and cyber security business, consisting of CrowdStrike, to “talk about concrete actions we will all require to enhance security and resiliency for our joint consumers,” Microsoft stated on Friday.
The event will occur on September 10 at Microsoft’s head office near Seattle, it stated in a post.
Bugs in the kernel can rapidly crash a whole os, activating the countless “blue screens of death” that appeared around the world after CrowdStrike’s defective software application upgrade was sent to customers’ gadgets.
Microsoft informed the Financial Times it was thinking about numerous choices to make its systems more steady and had actually not dismissed totally obstructing access to the Windows kernel– a choice some competitors fear would put their software application at a downside to the business’s internal security item, Microsoft Defender.
“All of the rivals are worried that [Microsoft] will utilize this to choose their own items over third-party options,” stated Ryan Kalember, head of cyber security technique at Proofpoint.
Microsoft might likewise require brand-new screening treatments from cyber security suppliers instead of adjusting the Windows system itself.
Apple, which was not struck by the interruptions, obstructs all third-party suppliers from accessing the kernel of its MacOS os, requiring them to run in the more restricted “user-mode.”
Microsoft has formerly stated it might refrain from doing the very same, after pertaining to an understanding with the European Commission in 2009 that it would offer 3rd parties the exact same access to its systems as that for Microsoft Defender.
Some specialists stated, nevertheless, that this voluntary dedication to the EU had actually not connected Microsoft’s hands in the method it declared, arguing that the business had actually constantly been totally free to make the modifications now under factor to consider.
“These are technical choices of Microsoft that were not part of [the arrangement],” stated Thomas Graf, a partner at Cleary Gottlieb in Brussels who was associated with the case.
“The text [of the understanding] does not need them to admit to the kernel,” included AJ Grotto, a previous senior director for cyber security policy at the White House.
Grotto stated Microsoft shared a few of the blame for the July interruption because the interruptions would not have actually been possible without its choice to permit access to the kernel.
While it may increase a system’s durability, obstructing kernel gain access to might likewise bring “genuine compromises” for the compatibility with other software application that had actually made Windows so popular amongst service clients, Forrester expert Allie Mellen stated.
“That would be an essential shift for Microsoft’s approach and service design,” she included.
Running specifically outside the kernel might reduce the danger of activating mass failures however it was likewise “really restricting” for security suppliers and might make their items “less reliable” versus hackers, Mellen included.
Running within the kernel provided security business more info about possible dangers and allowed their defensive tools to trigger before malware might take hold, she included.
An alternative choice might be to reproduce the design utilized by the open-source os Linux, which utilizes a filtering system that develops a segregated environment within the kernel in which software application, consisting of cyber defense tools, can run.
The intricacy of revamping how other security software application works with Windows indicates that any modifications will be tough for regulators to cops and Microsoft will have strong rewards to prefer its own items, competitors stated.
It “sounds great on paper, however the devil remains in the information,” stated Matthew Prince, president of digital services group Cloudflare.
© 2024 The Financial Times Ltd. All rights booked Not to be rearranged, copied, or customized in any method.
As an Amazon Associate I earn from qualifying purchases.